|

VPN Gate Overview
VPN Gate Academic Experiment Project is an online service
as an academic research at Graduate School of University
of Tsukuba, Japan. The purpose of this research is to expand
the knowledge of "Global Distributed Public VPN Relay
Servers" .
Why VPN Gate?
You can take these advantages
by using VPN Gate:
- You can get through the
government's firewall to browse restricted web sites (e.g.
YouTube).
- You can disguise
your IP address to hide your identity while
surfing the Internet.
- You can protect yourself
by utilizing its strong encryption while using public Wi-Fi.
Unlike traditional VPN services,
VPN Gate can get through most firewalls.
VPN Gate is free of charge. Not a single registration is required.
VPN Gate Public Relay Servers
There is a list of Public VPN Relay Servers on the VPN
Gate Academic Project Web Site.
Anyone online can
hook up to any VPN servers on the listthe list.
No
user registrations are required.
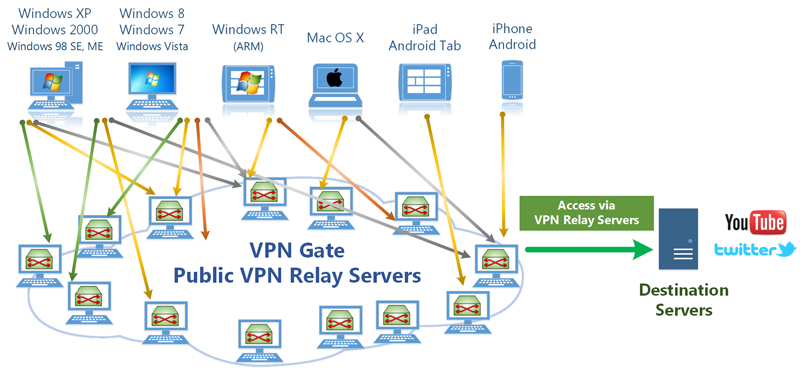
How does VPN Gate work?
-
VPN Gate network consists of many VPN servers, which are
provided by volunteers around the world.
You can provide your own computer as
a VPN server to join this experiment.
- Windows, Mac, iPhone, iPad and Android are
supported.
- Supports SSL-VPN (SoftEther VPN) protocol,
L2TP/IPsec protocol, OpenVPN protocol and Microsoft SSTP
protocol.
- Anonymous connections are accepted.
- No user registrations are required.
- Each VPN server has a dynamic IP address.
Therefore it may change at random period.
- VPN servers appear and disappear at any time.
Therefore, an IP address may not always connect
to a VPN server.
- All VPN servers are capable of routing your traffic
to the Internet, so you can disguise
your real IP address.
- Using a server located somewhere other than your
region may provide you some more accessible websites,
because the comminucation would look as if it is
originated from the country the VPN server resides.
The problem that this research solves
Out motivation to begin the VPN Gate Experiment are to
solve the following problems exists currently:
Problem #1. Governmental Firewall Blocks
Accesses to Certain Websites
The Internet is a revolutionary network to enable everyone
to communicate with each other with computers and servers without any
restriction. Any websites provided by individuals
or companies can be reached from anywhere around the
world. Everyone in the world is a potential customer of a
web service, so many web corporates are trying hard to
develop and improve their services.
This will make competitions between corporates worldwide,
helping their product become better and better, time after time.
Free competition around the globe is essential for improving
online services.
Internet provides such a great field for fair
competition. However, some countries are
attempting to disrupt fair competitions. For
example, great video-sharing sites such as YouTube, or
excellent SNS sites such as Twitter or Facebook are out.
However, some governments do not let their people access
these great websites within the country. Such filtes are commonly
called "Firewall" . People in such country
are often affected by the government's firewall.
In United States, Japan and most Europian countries, people
do not let their governments placing such firewall, as their
Constitutions state. However, it is said that some
other countries have such firewall for the sake of censorship.
The government's firewall forces their people to use only
domestic web services instead of those available around the world.
Under such control, people cannot visit global web services which compete
with domestic web services. In other words, such
government provides unfair advantages to the few domestic
web-service providers at the cost of convinience that would
have satisfied the users in that country. Ultimately,
such government's overprotection will
cause decline in public interests, as most people in such country
are kept away from the worldwide, valuable web services.
It is convenient for users behind the government's
firewall if they have freedom to access YouTube, Twitter,
Facebook or other wonderful web services. This will prompt
domestic web service providers which are overprotected by
the government's firewall to get involved in
the worldwide fair competitions. Ultimately,
the competitions will refine domestic web services
just like many worldwide web services, thus everyone will
be satisfied.
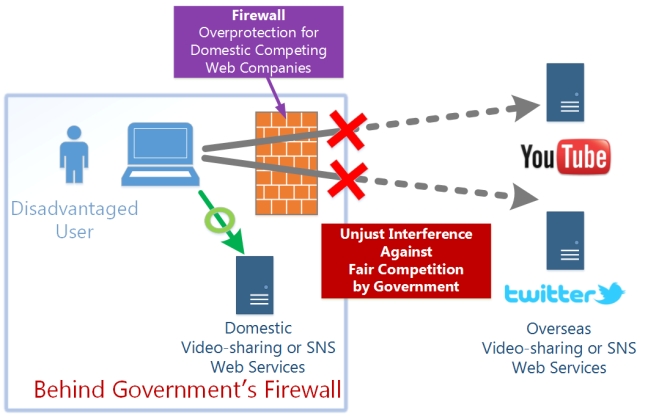
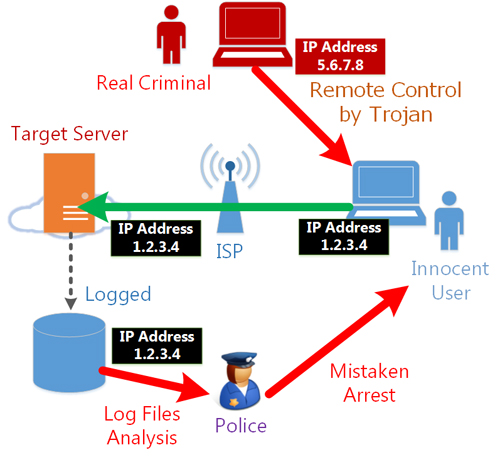
Problem #2. It is possible to identify an individual
by tracing the supposed IP address which is found in the
logs of the server.
If you access to a website, or send an email, your source
IP address will be logged on the destination web server, or
on the headers included in the payload of an email. An IP
address itself is not directly connected to a person, However,
an IP address can be traced to an individual who visits
multiple websites. This gives online advertisements an
advantage of tracking a person with a supposedly personalized ads.
Additionally, an IP address can be used to identify the
person who initiated a suspicious activity by investigation.
Police agencies, prosecutors or lawyers can abuse their privileges to request the logs
regarding the allocation of IP addresses, which are held by ISPs.
Such logs are normally kept private by ISPs.
However, once someone obtains the logs, one can investigate
who sent a particular email, who posted a certain message to a website, etc.
It might be abused to revenge to the one who conducted an
indictment for public interests. The risk of tracable IP address
is that it may discourage the good people to criticize wrong things.
Moreover, since an IP address and a person is considered linked
together, therefore the person who has had the IP address in question
is responsible of every communication it involved.
Recently we have seen a serious incident that our law enforcement
agencies had arrested an innocent person who allegedly sent
offensive contents to several companies. However, he has done nothing wrong--
it was all done by a remote person using a Trojan horse.
The innocent was finally released, but it
was one of the worst false accusation incidents in Japan's
recent history.
Therefore, a method to temporarily hide your real IP
address is favorable. The key benefits are anonymity,
untracability, and safety. You will stay low-profile,
be free from tracking advertisements, and be safe from
false charge, even if your computer is compromised by malwares.
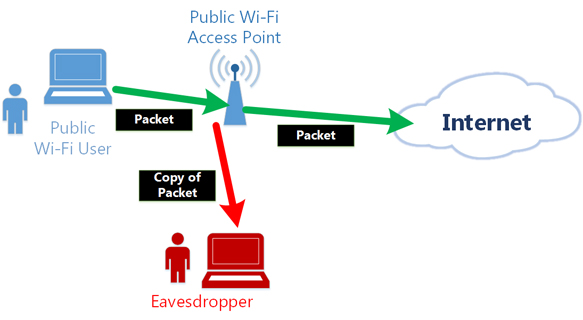
Problem #3. Public wireless networks are vulnerable to packet sniffing.
Most public Wi-Fi networks can be eavesdropped by anyone
as they are commonly unencrypted. Wired networks are also
vulnerable to eavesdropping when applied a technique, for
example, ARP spoofing.
Moreover, the network administrator or the facility owner
may have the opportunity to tap into your communication.
Even if you are hooking up to the Internet at your home,
there is a risk that the employee of your ISP or telecom
company might be wiretapping to observe your plaintext packets.
(In fact, there was a criminal incident that an employee of Nippon Telegraph and
Telephone Company had wiretapped in the building the company
resides. So we can never trust employees of ISPs or telecom
companies.)
When using HTTP, POP3 or IMAP in plaintext on
the Internet, you are vulnerable to eavesdropping. For example,
HTTP-over-SSL (HTTPS) is secure against eavesdropping, however, most web sites uses HTTP,
whose packets are transmitted in plaintext.
It is favorable that there may be a method to encrypt all
online activities automatically. When such technique is
applied, nobody can snoop into your transmissions.
VPN encrypts and relays your packets
VPN is the solution to all of these problems.
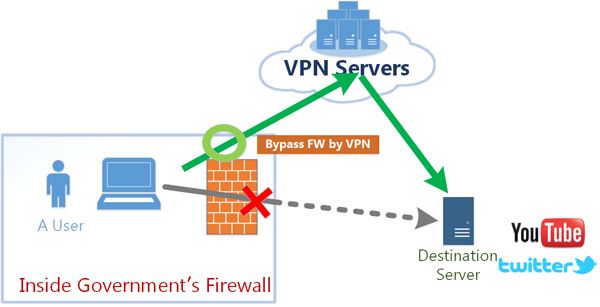
Benefit 1. VPN can bypass the governmental firewall.
If the governmental firewall is malfunctioning, or when
some websites abroad are unreachable within the firewall,
you can access them by relaying your connection to
VPN servers located outside of your territory of residence.
Benefit 2. VPN can hide your actual IP address.
While your connection is relayed through a VPN server,
the source IP address disclosed to the target server will be
the VPN server's, not your actual one. This will be very
helpful to you because nobody can trace back to your original
IP address, eliminating the risk of being spied on.
VPN enables you to post contents on BBS or send emails
completely anonymously, providing safety to just activists
who intend to bring an accusation for public benefits.
You will be safe from revenges or lawsuits by the accusee.
Finally, even if your computer has been compromised by a malware
and hijacked by a criminal, VPN protects you from being framed up
and thrown to jail because your actual IP address will be concealed.
Benefit 3. VPN can prevent eavesdropping.
When using VPN, all transmissions will be
automatically encrypted. Even if your local network is compromised
by snoopers, your transmissions will remain intact.
Note that this solution can only encrypt within the VPN tunnel,
therefore packets forwarded from the VPN server to the destination
are not within the scope of this solution. (i.e. it will not be encrypted.)
VPN Gate's advantage over traditional VPN services
As described above, VPN can solve many problems upon
using the Internet. However, normally you are required to
have at least one VPN server in a remote physical location (overseas) to
take advantage of the functions of VPN.
Most Internet users have difficulties to prepare their own VPN
servers in remote territories. There are, however, traditional paid
shared-VPN services for them which are provided by some
Internet companies. Such services require user
registrations and often with credit-card number for payment.
After registrations users will acquire the
right to utilize the shared VPN servers for a specific period according
to the contract.
So what are the differences between VPN Gate and such
traditional paid VPN services? The two seem to be similar when seen from
consumers. However, VPN Gate has more advantages over traditional
VPN services as described below.
Problems with traditional shared VPN services
traditional VPN services are hosted by companies
on their datacenters. This
traditional way of providing shared VPN servers
has a problem that the IP addresses of the VPN
servers are on the same or close IP address allocation
block, generally because the servers are hosted via the same ISP.
Also, these IP addresses are generally static, so they seldom change.
Such shared VPN service are weak against
"unknown trouble on the government's firewall" . The
"unknown trouble on the government's firewall" usually
exhibits problems that a certain IP address or a range of IP addresses
become completely unreachable from inside the protected area.
If the "unknown trouble" strikes the IP address
range of the IP address blocks of their VPN server
clusters, all VPN servers within the area become disabled.
In fact, recently it is reported that
one day a specific cluster of traditional shared VPN servers
became suddenly unreachable from a certain country which
has a governmental firewall running.
Another problem with the traditional shared VPN servers is
the conjunction of bandwidth. traditional shared VPN servers are
physically condenced inside a datacenter. All transmissions
made by their users will be concentrated on a certain line of
the datacenter's uplink. Also, all workloads affect the
physical servers that host the VPN servers. The service provider
may consider expanding the server clusters or enforcing the
uplink, however, such expansions are costly. The fee may increase
when such expansions are made, or otherwise, the speed may drop
due to cost reduction.
To sum up, most shared VPN services lack quality.
Advantages of VPN Gate Academic Experiment
As you can see on the List of VPN Gate
Public VPN Relay Servers, there are a lot of running VPN
Gate Public VPN Relay Servers. These VPN servers are neither
physically placed on a specific datacenter nor a specific IP
address range; they are hosted on different ISPs
and on a wide variety of physical locations.
Every VPN Gate Public VPN Relay Servers are distributed
and hosted by many volunteers. A volunteer is a person who
owns a computer which is kept hooked up to the broadband that
connects to the Internet. A volunteer agrees to provide the CPU
time and the bandwidth to support the VPN Gate Academic
Experiment. You can become a volunteer, too.
Volunteers are distributed throughout the world. The ISPs of
volunteers also vary. So IP addresses of every
VPN servers are distributed, showing no particular patterns of
their assigned IP addresses. The total number of volunteers changes
from time to time, so as the servers' IP addresses. Therefore, if
something wrong happens to the governmental
firewall, most VPN Gate servers should survive such incident.
If a few VPN Gate servers become unreachable, you may choose among
more servers located in a different territory.
VPN Gate is available free of charge, because
our servers are hosted by volunteers and they do not spend very much
for bandwidths and CPU times for the servers they have.
Not only that it is free, but also you are not required to
register a user account upon using this service.
To sum up, unlike the traditional shared VPN services, the
VPN Gate Academic Experiment Service can be used at no costs.
Mirror servers of VPN Gate web site
Once you successfully establishes a VPN session to one of the VPN Gate
Public VPN Relay Servers, you will gain the freedom to access the
Internet from any country.
However, if the www.vpngate.net web site (this web site)
is unreachable from your country, you may not be able to obtain
the VPN Gate Public VPN Relay Servers List
at first.
So we are providing many Mirror Sites
to help users who are suffering from such difficulties. If you
can access at least one of these mirror sites, you
can browse the VPN Gate Public VPN Relay
Servers List page.
If you are a resident of the country which has a governmental
firewall which exhibits unknown errors preventing accesses to the
www.vpngate.net, please take a look at
the Mirror Sites List page. You may copy the URL
list and paste it onto SNS, Blogs or community forums of your
country to help VPN users in your country.
VPN Gate is an extended plug-in for SoftEther VPN
Software
Visit our another VPN
project, "SoftEther Project".
This is the parent project. VPN Gate is a child project of
SoftEther Project.
|